CMVP Testing
What is CMVP?
・CMVP stands for Cryptographic Module Validation Program.
・The program was initiated in 1995 by NIST, as a joint program with CSE, a Canadian government agency, for the purpose of government procurement of secure cryptographic products. In Canada, the program is currently operated by the Canadian Centre for Cyber Security (CCCS), the Canadian government agency.
・The FIPS 140-3 (SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES) is the de facto standard for cryptographic module.
・CMVP is a mandatory requirement for US and Canadian government procurement of cryptographic products.
・No. 11 of The National Security Telecommunications and Information Systems Security Policy (NSTISSP) requires CMVP for US Government procurement of cryptographic products.
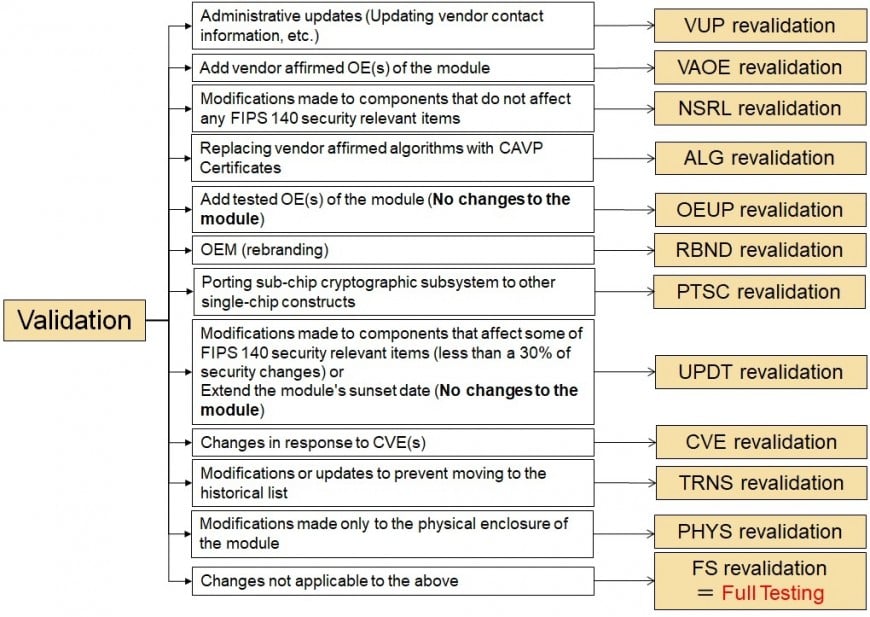
What is CMVP revalidation?
・The procedure of placing a new brand, version or model of an already validated cryptographic module on the CMVP Validation List is called revalidation.
・Compared to new testing, the time required for testing and the testing workload can be reduced. (e.g. reduced testing costs)
・The applicable scenario depends on what changes are made to the product.
・In the validation process by the CMVP(Report review), the review of revalidation takes precedence over initial validation.
Documentation to be provided by the applicant
The documents and other materials to be prepared by the applicant are generally as follows. They do not have to be all in place at the start of the test, but the test is not complete until they are all in place.
・ VE Answer Document
・ Security policy
・ Finite State Model (FSM)
・ Configuration management documents
・ Functional specifications
・ Source code (or HDL code)
・ Administrator guidance
・ User guidance
・ Vendor test documentation
Test duration and cost
The duration and cost of the test will depend on the following factors, i.e. a rough estimate can be made with information on the following factors.
・ Security level for which validation is desired.
・ Type of cryptographic module (hardware, software, firmware, etc.).
・ Type and number of cryptographic algorithms implemented in cryptographic modules.
・ Type and number of cryptographic services implemented in cryptographic modules.
・(For software) Type and number of operating systems on which the cryptographic module can operate.
Inquiry For evaluation or testing requests, questions or consultation inquiries, please contact. ■ Email labinquiry@ecsec.jp |